Many organizations are required to comply with information protection standards whether mandated by law, executive order, or their own policies. To address this demand, Microsoft has developed Sensitivity Labels located within the Microsoft 365 Compliance Center.
This guide will assist administrators configuring an M365 tenant to enable Sensitivity Labels within Microsoft 365 groups (aka Modern Groups, M365 Groups, O365 Groups, Unified Groups).
Note: To leverage Sensitivity Labels for M365 Groups, an Azure Active Directory Premium P1 license must be present within the tenant. It does not have to be assigned to a specific user.
Validate Sensitivity Labels for M365 Groups are Enabled
We must first ensure that sensitivity labels are enabled within the tenant. If this setting has not been enabled, then when attempting to create an M365 group within Azure AD, the screen will appear as follows:

To verify or enable sensitivity labels for M365 groups, connect to the tenant’s Azure AD instance via PowerShell. Use the following commands to first establish a connection to the tenant:
Set-ExecutionPolicy RemoteSigned
Install-Module AzureADPreview -Force
Import-Module AzureADPreview
Connect-AzureAD
Next, obtain the current group settings for the Azure AD organization:
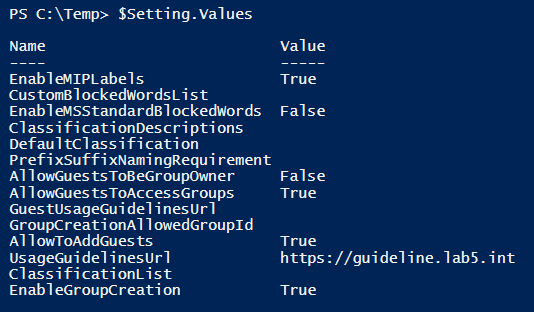
$setting = Get-AzureADDirectorySetting -Id (Get-AzureADDirectorySetting | where -Property DisplayName -Value “Group.Unified” -EQ).id
$setting.values
Note: If this setting has not been previously configured, an error may appear:

If this error is encountered, you must first configure group settings for Azure AD Tenant. See Appendix A for instructions on how to perform this task.
If the object EnableMIPLabels has a value of False, then Sensitivity Labels are not enabled. To enable sensitivity labels for M365 groups, execute the following commands:
$Setting[“EnableMIPLabels”] = “True”
Set-AzureADDirectorySetting -Id $Setting.Id -DirectorySetting $Setting
Note: Sensitivity labels must be scoped to protect Groups. This is accomplished within the Microsoft 365 Compliance Center. To view how to scope sensitivity label protection for groups see Appendix B.
Conclusion
Now that Sensitivity Labels have been enabled for M365 Groups, the option to apply a Sensitivity Label will appear. This is true both within Azure AD and the Microsoft 365 Admin Center. See below:
Microsoft Azure AD Admin Center:

Microsoft 365 Admin Center:

Appendix A – Configure Group Settings for Azure AD Tenant
Ensure that an established connection has been made to the Azure AD instance for the tenant:
Set-ExecutionPolicy RemoteSigned
Install-Module AzureADPreview -Force
Import-Module AzureADPreview
Connect-AzureAD
Next, obtain the template settings and create a new settings object based on the correct template:
$TemplateId = (Get-AzureADDirectorySettingTemplate | where {$_.DisplayName -eq “Group.Unified”}).Id
$Template = Get-AzureADDirectorySettingTemplate | where -Property Id -Value $TemplateId -EQ
$Setting = $Template.CreateDirectorySetting()
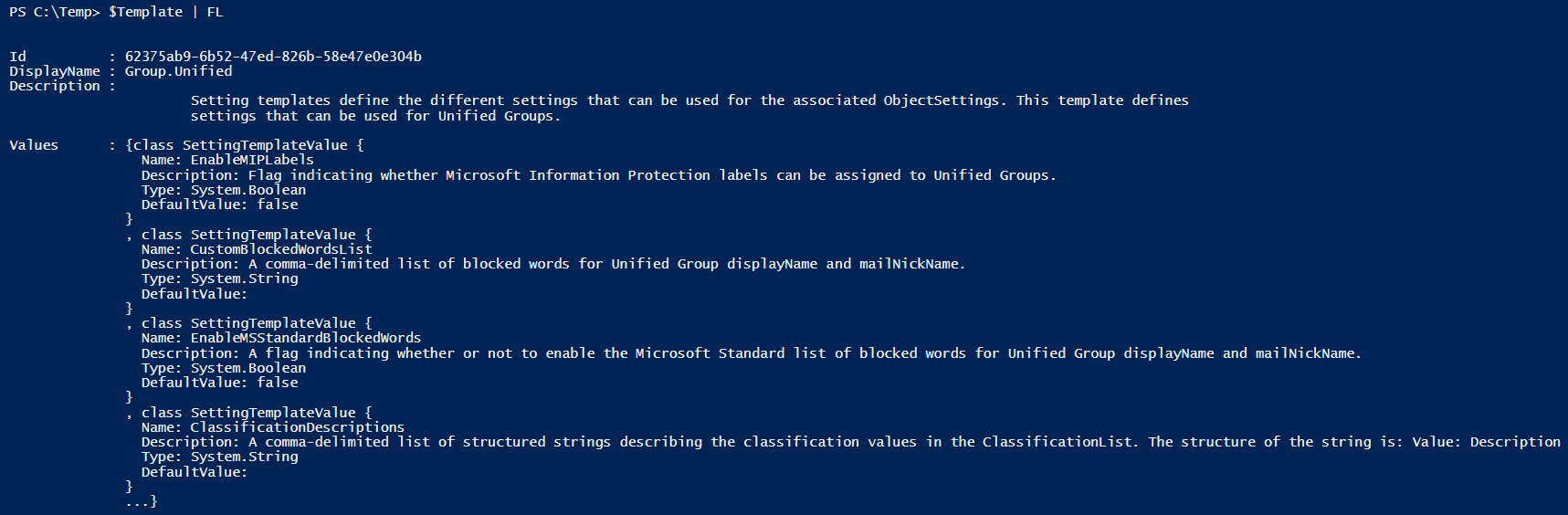
To view the current configuration of the template by outputting the value of the $Template variable to Format-List:
$Template | FL
Having now created the settings object, we are now able to update values within the object. Of specific importance are the following objects:
- UsageGuidelinesUrl: This should point to the URL which outlines the appropriate usage of the M365 Groups.
- EnableMIPLables: This is the object setting which enables Sensitivity Labels.
Run the following commands to configure the specific object values:
$Setting[“UsageGuidelinesUrl”] = “https://guideline.lab5.int”
$Setting[“EnableMIPLabels”] = “True”
Finally, update the template settings for the Group.Unified template:
New-AzureADDirectorySetting -DirectorySetting $Setting
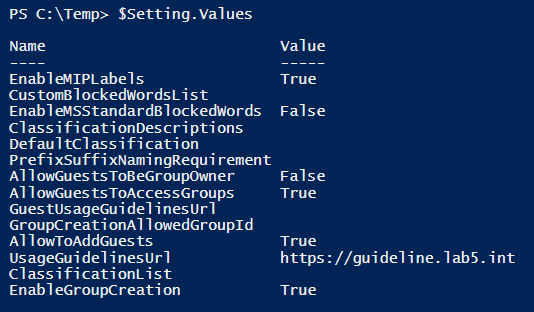
To view the now configured settings for the tenant, run the following commands:
$Setting = Get-AzureADDirectorySetting | ?{$_.DisplayName -eq “Group.Unified”}
$Setting.Values
Appendix B – Scope Sensitivity Labels for Groups
Sensitivity labels must be scoped to protect Groups. This is accomplished within the Microsoft 365 Compliance Center. Upon accessing the Compliance center, expand Solutions, then select Information Protection.
At this point, creating or modifying a sensitivity label will both work. For the purpose of this demonstration, an existing group will be modified.

On the Scope options page, ensure to enable Groups & sites.

On the Define protection settings for groups and sites,

Selecting the Privacy and external user access settings will provide the following options:

Selecting the Define external sharing and device access settings will provide the following options:

References
Reference 1: Enable Sensitivity Label Support
Reference 2: Configure Group Settings for Azure AD Tenant
Reference 3: Group Template Settings
Reference 4: NIST SP 800-171 Rev. 2